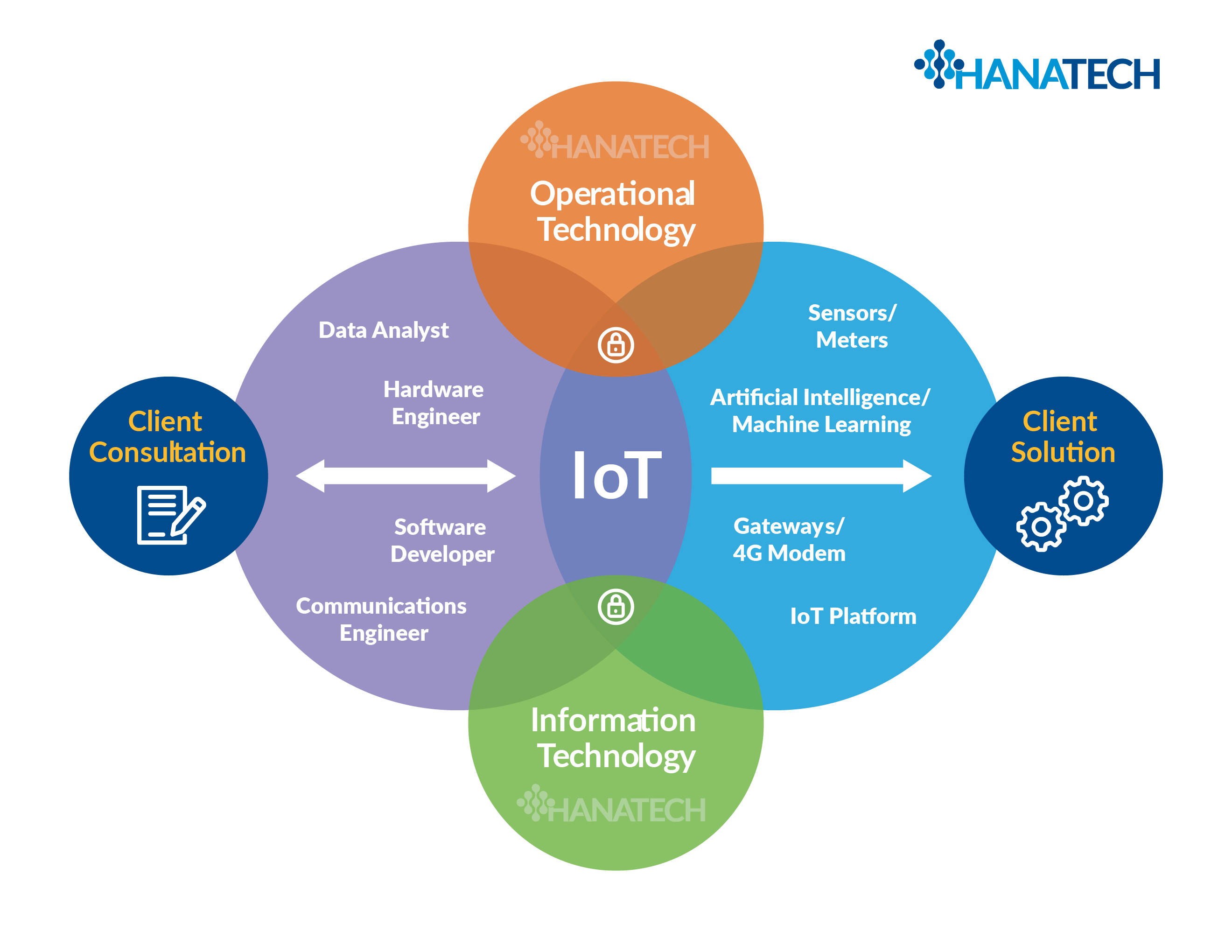
How To Manage IoT Behind Firewall: A Comprehensive Guide
Let’s face it, folks—IoT devices are everywhere these days. From smart thermostats to industrial sensors, they’re revolutionizing the way we live and work. But here’s the catch: managing IoT behind a firewall isn’t as simple as plugging in a device and calling it a day. Security, connectivity, and performance are all critical factors that need your attention. In this article, we’ll dive deep into how to manage IoT behind a firewall with practical examples that you can implement today.
Managing IoT devices isn’t just about setting up a network; it’s about ensuring your data stays safe while maintaining seamless communication. The rise of IoT has brought incredible opportunities, but it also comes with its own set of challenges. From unauthorized access to data breaches, the risks are real. That’s why understanding how to manage IoT behind a firewall is more important than ever.
In this guide, we’ll cover everything from setting up firewalls to securing IoT devices, all while keeping your network humming along smoothly. Whether you’re a tech enthusiast or a seasoned IT pro, this article will give you the tools you need to take control of your IoT ecosystem. So buckle up and let’s get started!
- Kannada Movies 2024 Streaming 4movierulz Whats New
- Latest Telugu Movies Reviews Streaming News Yearly Guide
Why Managing IoT Behind a Firewall Matters
Before we jump into the nitty-gritty, let’s talk about why managing IoT behind a firewall is such a big deal. Think about it: your IoT devices are constantly transmitting data. This data could be anything from temperature readings to sensitive financial information. Without proper security measures, your network could be wide open to hackers. Yikes, right?
Managing IoT behind a firewall helps protect your devices and data from unauthorized access. It also ensures that your network remains stable and efficient. By implementing the right strategies, you can prevent downtime, reduce security risks, and keep your IoT devices running smoothly.
Here’s a quick rundown of the key benefits:
- Xxx Movie Mania Dive Into Adult Entertainment Now
- Kranti 2023 Watch Kannada Movie Online Free The Truth
- Enhanced security for your IoT devices
- Improved network performance
- Reduced risk of data breaches
- Streamlined management of your IoT ecosystem
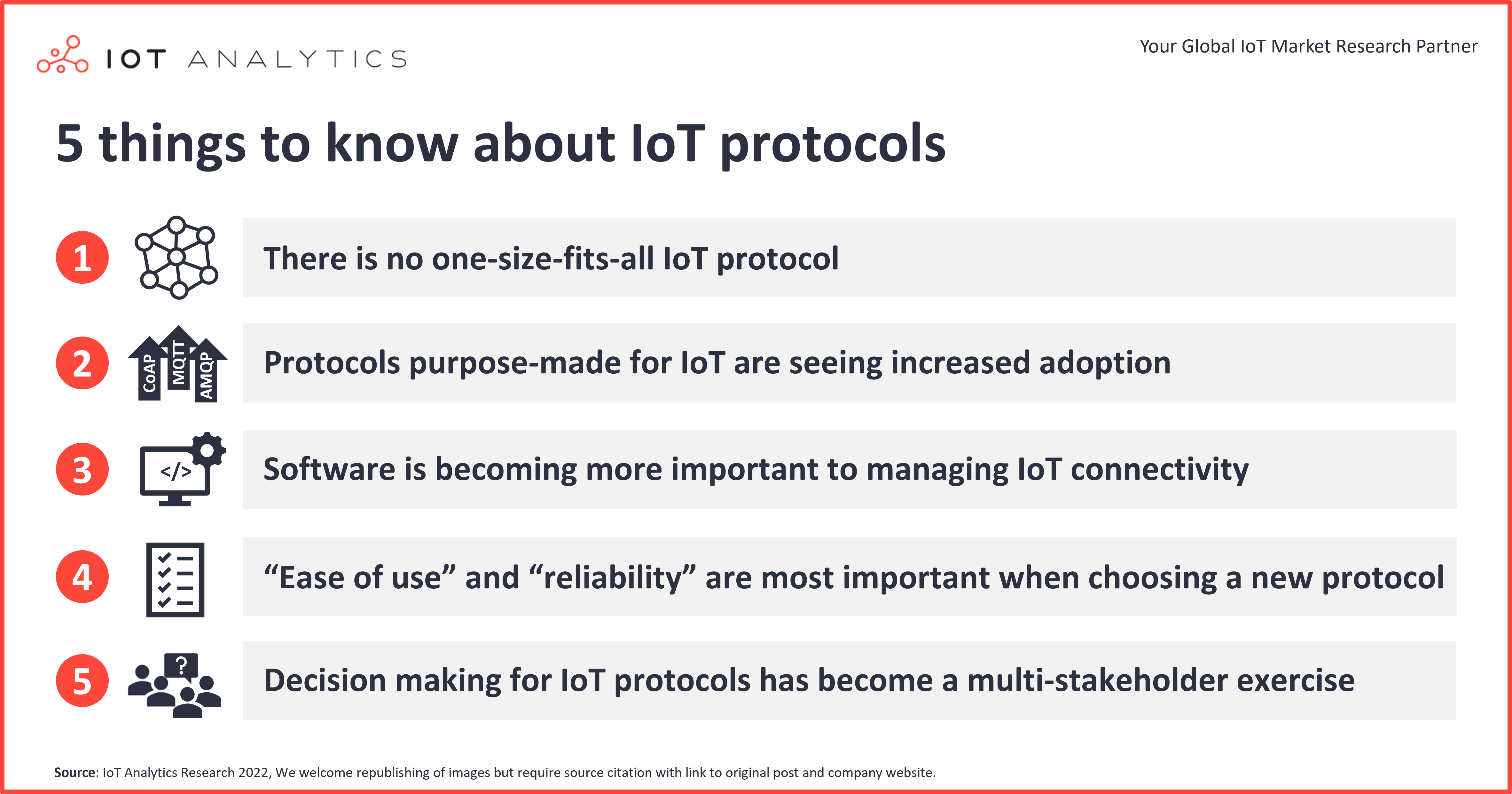
Understanding Firewalls and IoT
Okay, so what exactly is a firewall, and how does it relate to IoT? Simply put, a firewall is like a digital bouncer that controls who gets in and out of your network. It monitors incoming and outgoing traffic, blocking anything suspicious. When it comes to IoT, firewalls play a crucial role in protecting your devices from external threats.
Now, here’s the thing: not all firewalls are created equal. Some are better suited for IoT environments than others. For example, next-generation firewalls (NGFWs) offer advanced features like deep packet inspection and application awareness, making them ideal for managing IoT devices. These firewalls can identify and block potential threats before they even reach your network.
Types of Firewalls for IoT
Let’s break down the different types of firewalls you can use to manage IoT devices:
- Packet Filtering Firewalls: These basic firewalls inspect individual packets of data and decide whether to allow or block them based on predefined rules.
- Stateful Inspection Firewalls: These firewalls keep track of active connections, allowing them to make more informed decisions about which packets to allow.
- Next-Generation Firewalls (NGFWs): These advanced firewalls offer features like intrusion prevention, application awareness, and deep packet inspection, making them perfect for IoT environments.
Setting Up a Firewall for IoT Devices
Alright, let’s get practical. How do you actually set up a firewall to manage your IoT devices? The process may vary depending on the type of firewall you’re using, but here’s a general outline to get you started:
- Identify all the IoT devices on your network.
- Determine which devices need access to the internet and which ones don’t.
- Set up rules in your firewall to allow or block specific types of traffic.
- Regularly update your firewall rules to reflect any changes in your IoT ecosystem.
Remember, the key to a successful setup is to be thorough. Don’t skip any steps, and make sure you test everything before going live. Trust me, it’s better to catch any issues now than to deal with a security breach later.
Best Practices for Firewall Configuration
Here are some best practices to keep in mind when configuring your firewall for IoT:
- Use strong, unique passwords for all your devices and firewall settings.
- Enable multi-factor authentication whenever possible.
- Regularly update your firewall software to ensure you have the latest security patches.
- Monitor your firewall logs for any suspicious activity.
Securing IoT Devices Behind a Firewall
Now that we’ve covered the basics of setting up a firewall, let’s talk about securing your IoT devices. Security isn’t just about having a firewall in place; it’s about taking a holistic approach to protecting your entire IoT ecosystem.
Here are a few tips to help you secure your IoT devices:
- Change default passwords on all your devices.
- Disable any features or services you don’t need.
- Regularly update your devices with the latest firmware.
- Use encryption to protect sensitive data.
By following these tips, you can significantly reduce the risk of unauthorized access and data breaches. Remember, security is an ongoing process, so don’t get complacent. Stay vigilant and keep your defenses up to date.
Common IoT Security Threats
Let’s take a moment to discuss some of the most common IoT security threats:
- Malware: Malicious software that can infect your IoT devices and spread throughout your network.
- Botnets: Networks of compromised devices used to launch large-scale attacks.
- Man-in-the-Middle (MitM) Attacks: Attackers intercept and alter communication between devices.
- Denial-of-Service (DoS) Attacks: Attackers flood your network with traffic, causing it to crash.
Understanding these threats is the first step in protecting your IoT devices. By staying informed and taking proactive measures, you can keep your network safe from harm.
Managing IoT Behind a Firewall: Real-World Examples
Talking about theory is great, but let’s see how managing IoT behind a firewall works in the real world. Here are a couple of examples to give you a better understanding:
Example 1: A Smart Home Environment
Imagine you’re managing a smart home with multiple IoT devices, including smart lights, thermostats, and security cameras. To keep everything secure, you could set up a firewall that allows only specific devices to access the internet. For example, you might allow your security cameras to stream footage to a cloud server but block your smart lights from accessing external networks. This way, you ensure that only the necessary devices have internet access, reducing the risk of unauthorized access.
Example 2: An Industrial IoT Setup
In an industrial setting, managing IoT behind a firewall becomes even more critical. Picture a factory with hundreds of IoT sensors monitoring equipment performance. By setting up a robust firewall, you can ensure that only authorized personnel have access to the data these sensors collect. You can also configure the firewall to block any unauthorized attempts to access the network, keeping your operations running smoothly.
Tools and Technologies for Managing IoT Behind a Firewall
When it comes to managing IoT behind a firewall, having the right tools and technologies can make all the difference. Here are a few options to consider:
- Network Segmentation: Divide your network into smaller segments to isolate IoT devices from other systems.
- Intrusion Detection Systems (IDS): Monitor your network for suspicious activity and alert you to potential threats.
- IoT Device Management Platforms: Use platforms like AWS IoT or Microsoft Azure IoT to manage your devices more efficiently.
By leveraging these tools, you can streamline your IoT management process and enhance your network’s security. Just remember to choose tools that align with your specific needs and budget.
Choosing the Right Tools for Your Needs
Selecting the right tools for managing IoT behind a firewall can be overwhelming, especially with so many options available. Here are a few factors to consider:
- Scalability: Can the tool grow with your IoT ecosystem?
- Compatibility: Does it work with your existing infrastructure?
- Cost: Is it within your budget?
- Support: Does the vendor offer reliable customer support?
Troubleshooting Common Issues
Even with the best planning and tools, issues can still arise. Here are some common problems you might encounter when managing IoT behind a firewall and how to troubleshoot them:
- Device Connectivity Issues: Check your firewall rules to ensure they’re not blocking necessary traffic.
- Slow Network Performance: Optimize your firewall settings to improve network efficiency.
- Security Breaches: Review your firewall logs to identify and address any vulnerabilities.
By addressing these issues promptly, you can keep your IoT ecosystem running smoothly and avoid costly downtime.
Future Trends in IoT and Firewall Management
As technology continues to evolve, so do the trends in IoT and firewall management. Here are a few things to keep an eye on:
- AI-Powered Firewalls: Firewalls equipped with artificial intelligence can detect and respond to threats in real time.
- 5G Networks: The rise of 5G will enable faster and more reliable communication between IoT devices.
- Edge Computing: Processing data closer to the source can improve performance and reduce latency.
Staying informed about these trends will help you stay ahead of the curve and make the most of your IoT investments.
Preparing for the Future
To prepare for the future of IoT and firewall management, consider the following:
- Invest in cutting-edge technologies like AI-powered firewalls and edge computing solutions.
- Stay up to date with the latest trends and best practices in IoT security.
- Continuously educate yourself and your team about emerging threats and mitigation strategies.
Conclusion
Managing IoT behind a firewall isn’t just a nice-to-have; it’s a necessity in today’s connected world. By understanding the importance of firewalls, securing your devices, and leveraging the right tools and technologies, you can create a robust and secure IoT ecosystem. Remember, security is an ongoing process, so stay vigilant and keep your defenses up to date.
So, what are you waiting for? Take action today and start managing your IoT devices with confidence. Don’t forget to leave a comment below and share this article with your friends and colleagues. Together, we can build a safer and more connected future!
Table of Contents
- Why Managing IoT Behind a Firewall Matters
- Understanding Firewalls and IoT
- Setting Up a Firewall for IoT Devices
- Securing IoT Devices Behind a Firewall
- Managing IoT Behind a Firewall: Real-World Examples
- Tools and Technologies for Managing IoT Behind a Firewall
- Troubleshooting Common Issues
- Future Trends in IoT and Firewall Management
- Conclusion
Article Recommendations
- Stream Movies Shows Netflix Movierulz More 2024 Guide
- Unveiling Onlyfans Search Issues What Went Wrong

Detail Author:
- Name : Blake Waters
- Username : jfisher
- Email : lynn.schuppe@gmail.com
- Birthdate : 1999-02-14
- Address : 3231 Napoleon Gardens North Bennett, GA 74724
- Phone : +1-602-423-2740
- Company : Murazik Group
- Job : Separating Machine Operators
- Bio : Ut quaerat autem harum voluptas hic qui. Ullam et quis veritatis officiis necessitatibus. Dolorem aliquid dolores corporis.
Socials
tiktok:
- url : https://tiktok.com/@schuster1986
- username : schuster1986
- bio : Dignissimos ullam quas omnis non necessitatibus animi.
- followers : 860
- following : 53
linkedin:
- url : https://linkedin.com/in/schuster2024
- username : schuster2024
- bio : Autem veniam odio rerum sit qui.
- followers : 6034
- following : 108